Download
ipv6_surface_analyzer_1.0.tar.gz
Quick Start
- make sure that nmap, ifconfig & arping are installed and in your path
- run as root
tested on Ubuntu 11.10 64b
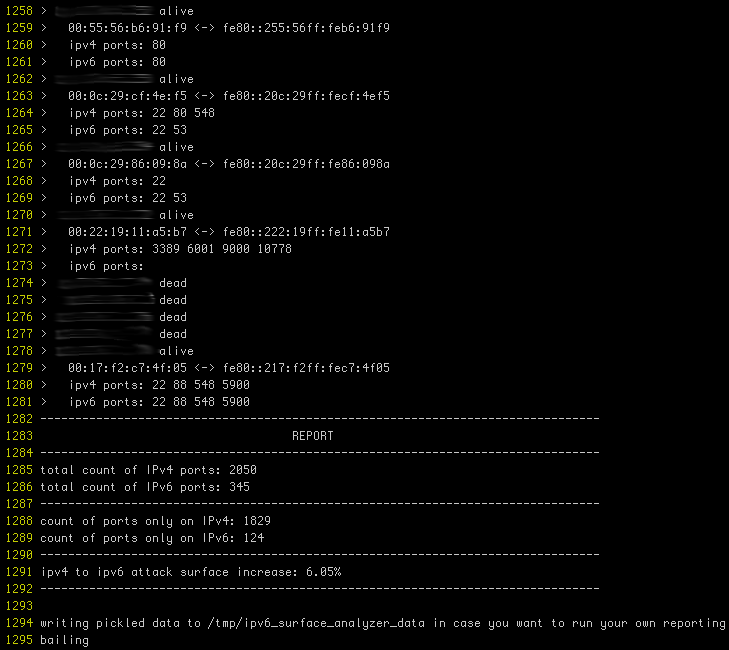
Screenshot
(actual ips obfuscated)
Purpose
With more devices coming IPv6 ready out of the box, a shadow network is emerging that nobody is paying attention to.
There’s Joe sysadmin, configuring a tight firewall for this new server, default deny, very restrictive & all. This is great but did he realize that there is nothing in front of IPv6? We are used to setting up iptables, ipfw, et cetera. Unfortunately ip6tables & ip6fw too often get forgotten.
With IPv4, a device was manually configured or wasn’t configured until it got an address from DHCP. With IPv6 a device that is not manually configured will hop on the network with a link-local address and try to further discover its settings. In fact, IPv6 reserves a range of addresses for network discovery, these link-local addresses are based on the device’s mac address.
Here is what ipv6_surface_analyzer.py does:
- iterate through a given IPv4 range
- for each address in the range, discover if a host sits behind it
- port scan potentially found host on IPv4
- infer IPv6 link-local address of host based on its mac address
- port scan inferred IPv6 address
The purpose of which is to establish by how much your attack surface is augmented by link-local IPv6.
This threat threat is somewhat mitigated by its local nature and there are 2 reasons why:
- link-local isn’t routed and thus your visibility is bound to networks you have a presence on.
- Getting a host’s mac address is only possible while being on the same network.
Local as it may be, having a shadow network providing a way to circumvent firewalls is quite risky.
Adapted for Mac OS X: http://tinypaste.com/aad585d9
Needs arping from MacPorts (probably BSD’s version)