I have recently acquired 5 Foscam FI8918W ip cameras for monitoring my house.

While this may seem like a step towards wearing a tinfoil hat, I have several reasons for doing so:
- It’s a fun geek project that is a subset of a larger endeavor to wire my house (think remote control)
- I love to know when the UPS guy dropped a package so I don’t have hundreds of dollars worth of electronics sitting on my front porch
- I get to know how the freaking chicken get out of their cage
- I get to know when the fucking raccoon is doing his patrol at night so I can shoot it in the face
- I would like to do fast motion videos of the garden through the seasons
- And yeah I’ll admit it, I like to keep an eye on stuffs
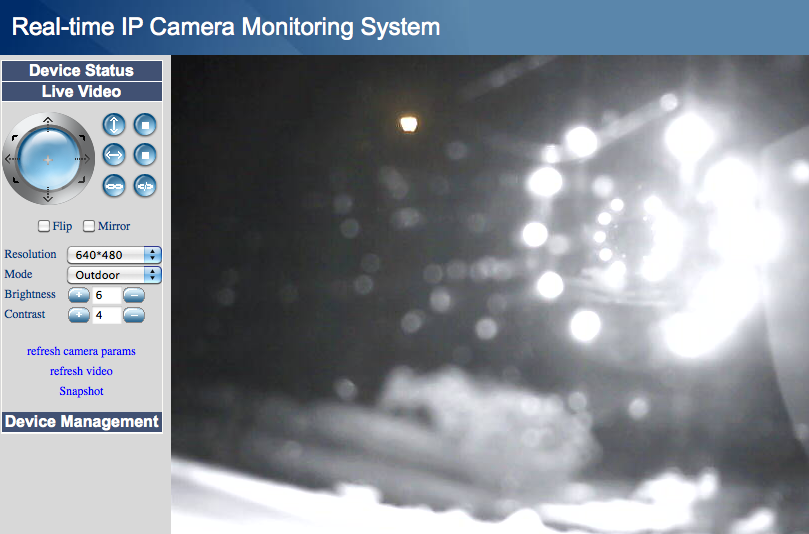
These little cams are absolutely great, some key features include: cat5 & wifi (wep, wpa, wpa2) network access, nightvision, pan 300 degrees, tilt 120 degrees, remote control & view. I wish I had bought a couple of outside ones though. The problem with most cameras is that they do night vision by shining some infrared LEDs, if your camera is inside pointing outside, the IR will get reflected by the window and the outside won’t be visible. I have yet to mess with the angles and such to try and fix that.
What an inside camera pointed at the outside looks like at night
The web interface for the cams is great, although not all the features are supported in browsers other than IE (for example sound, microphone and multicam) but video & remote control are fine.
If you want to record what the cams see, you’ll want a server on your network. In my case I use my Linux box and run the following script every hour:
pkill -9 wget
nohup wget http://<cam1_ip>/videostream.asf?user=<username>&pwd=<password> -O /cameras/cam1_`date +%F_%T`.asf > /dev/null 2>&1 &
nohup wget http://<cam2_ip>/videostream.asf?user=<username>&pwd=<password> -O /cameras/cam2_`date +%F_%T`.asf > /dev/null 2>&1 &
nohup wget http://<cam3_ip>/videostream.asf?user=<username>&pwd=<password> -O /cameras/cam3_`date +%F_%T`.asf > /dev/null 2>&1 &
nohup wget http://<cam4_ip>/videostream.asf?user=<username>&pwd=<password> -O /cameras/cam4_`date +%F_%T`.asf > /dev/null 2>&1 &
nohup wget http://<cam5_ip>/videostream.asf?user=<username>&pwd=<password> -O /cameras/cam5_`date +%F_%T`.asf > /dev/null 2>&1 &
rm /cameras/cam*_`date --date="5 days ago" +%F_`*.asf
This hourly rotation makes it convenient to quickly locate a file pertaining to an event you’re interested in. I am removing files older than 5 days but this can easily be adjusted on the last line. The directory where this all ends up is exported to a web server for remote access which yields the following results:
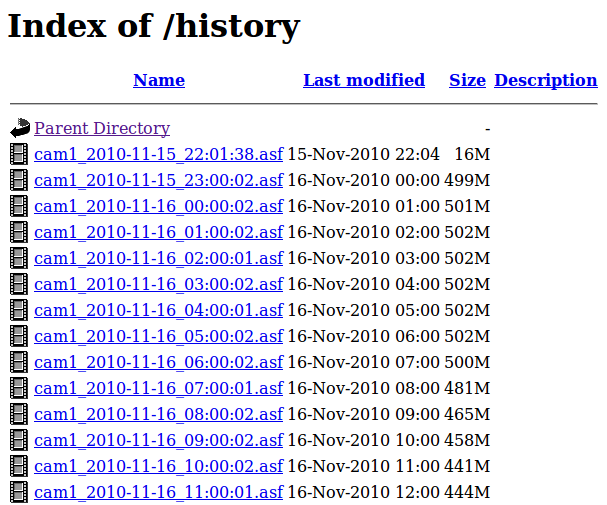
As you can see, an hour on 1 cam takes about 500M of disk space. This is because the cams do not have the processing power to compress the video stream, and this is fine by me, I don’t want them doing anything of the sort. The hourly cron could very well be augmented to encode new files but storage is cheap, my server not beefy and 5 days are more than enough for me.
As for making the cameras themselves available on the web, this frankly takes some guts. This is obviously a very critical device that you do not want anybody to have access to. One could simply forward some ports on their routers and rely on the cam’s authentication mechanism (make sure to change the default of admin/<blank>…). I don’t want the cams to even face the world where they are susceptible to exploits and bruteforce attacks so I proxy their access through my web server. This allows me to restrict IP access (default deny of course). I am also able to keep an eye on the logs and in general adds a layer of protection.
Here is the .htaccess file that does this magic for one of the cams (you’ll need to have mod_proxy enabled)
Options +FollowSymLinks
RewriteEngine On
RewriteBase /
RewriteRule ^(.*)$ http://<cam_ip>/videostream.cgi?user=<username>&pwd=<password> [P]
Foscam made it really easy to mess with the cam, all of the options that are available through their web interface are also available through direct URL calls which makes it easy to integrate the camera functionalities in a script (like the recording above). I’ve even started writing my own web interface for semi-public access that allows for visual customization as well and very granular function control.
the following URLs can be appended with “&user=<username>&pwd=<password>” so as to authenticate directly.
- http://<cam_ip>/snapshot.cgi gives you the current image
- http://<cam_ip>/video.cgi gives you live video
- http://<cam_ip>/live.htm gives you live video
- http://<cam_ip>/set_misc.cgi?ptz_patrol_rate=20 lets you change the rotation speed of the motors.
- http://<cam_ip>/set_misc.cgi?ptz_center_on_start=0 turns off the initial power-on rotation
- http://<cam_ip>/set_misc.cgi?led_mode=2 disables the front status LED
- http://<cam_ip>/reboot.cgi will reboot the cam
- http://<cam_ip>/decoder_control.cgi?command=0&onestep=1 tilts up
- http://<cam_ip>/decoder_control.cgi?command=2&onestep=1 tilts down
- http://<cam_ip>/decoder_control.cgi?command=4&onestep=1 tilts left
- http://<cam_ip>/decoder_control.cgi?command=6&onestep=1 tilts right
- http://<cam_ip>/set_misc.cgi?ptz_auto_patrol_type=1 sets the patrol type, possible values: 0: none; 1: horizontal; 2: vertical; 3: horizontal + vertical
- http://<cam_ip>/get_misc.cgi displays functional values
- http://<cam_ip>/get_log.cgi displays access log
- http://<cam_ip>/get_params.cgi displays configuration values
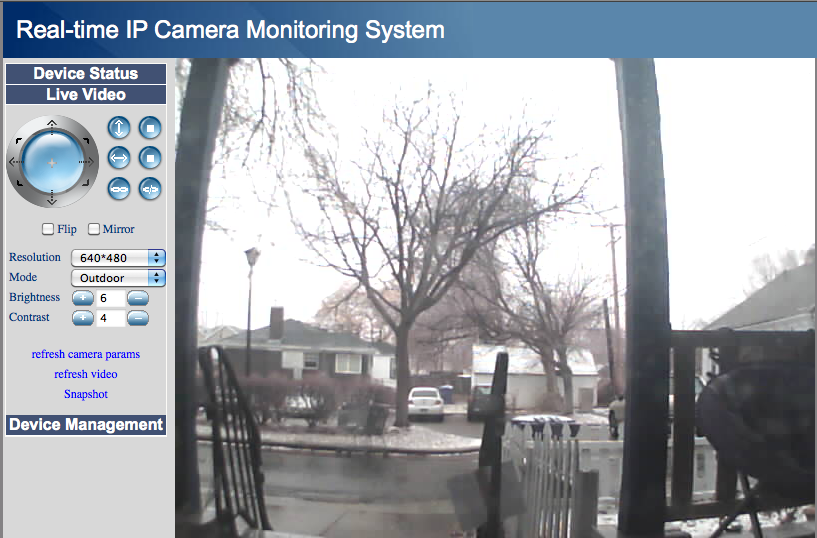
I’m very happy with them, they’re great products and fun to play with. One downside is their microphones which are pretty horrible but I don’t care much about sound. Here are a few pictures of them in action:
Inside cam pointed outside during the day
Nightvision in the chicken coop
[flv:http://ben.akrin.com//wp-content/uploads/2010/11/New-Project.flv 640 480]




